Cyber News
CESIN Barometer 2026: analysis of cyber threats and cybersecurity trends in France
The CESIN 2026 barometer reveals a paradoxical trend in corporate cybersecurity: while the number of significant cyberattacks is decreasing, their consequences are becoming considerably more severe.
This annual study by the Club des Experts de la Sécurité de l'Information et du Numérique (Club of Information and Digital Security Experts) is an essential reference for understanding the evolution of cyber threats in France.
.png)
.png)
The purpose of this article is to provide you with a clear and practical overview of the Cyber Resilience Act.
At the end of the document, you will also find advice on how to structure your approach and facilitate compliance.

With digital transformation and the rise in cyberattacks, issues relating to traditional IT management and corporate cybersecurity can overlap.

Tenacy is proud to be an official sponsor of CESIN —a partnership we will continue in 2026, marking our ongoing commitment to the cybersecurity community in France.
.png)
Ah, the eternal dilemma between risk management and compliance... Companies often pit them against each other, and the tools available on the market tend to reflect this dichotomy. However, the two approaches are complementary in the context of your cybersecurity strategy. This is illustrated by the famous ANSSI pyramid: compliance is a necessary foundation for addressing major risks.

Ensuring the security of information systems requires strict compliance with the standards and constraints applicable to each sector of activity and each organization. Chief Information Security Officers (CISOs) and Data Protection Officers (DPOs) each contribute their expertise to serve this common goal.

We are proud to announce that Tenacy has been named Top Startup 2025 in Lyon by LinkedIn News, making it one of the five most dynamic startups in the Lyon ecosystem! This prestigious ranking highlights fast-growing local startups that are innovating in their sectors and attracting the best talent.

Are you preparing for an ISO 27001 certification audit? This process, which is the result of extensive work on your ISMS, can be particularly stressful. So, what are the steps you need to know? And how can you ensure you are ready to obtain your certification? We have broken down the audit process in detail with the help of Mathieu Briol, a qualified ISO 27001 auditor.

In order to oversee cybersecurity measures within a company, the management committee must first define its vision. This vision is formalized in a document simply called the information system security policy.

From assessing the state of IT security to analyzing previous attacks, mapping critical assets, and continuing past actions related to risk analysis, the first 100 days of a CISO's tenure are crucial for the organization.
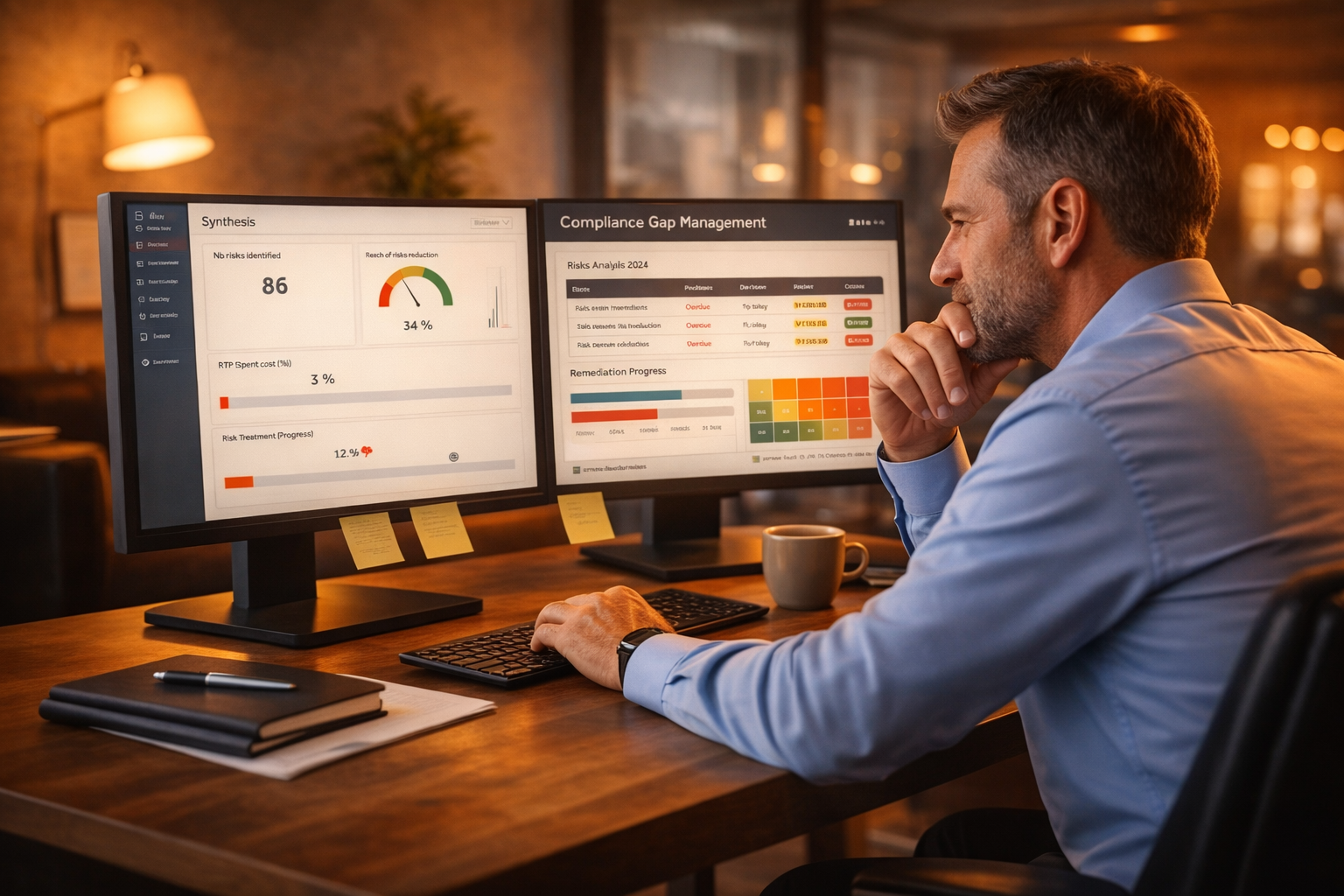
In an ever-changing regulatory landscape, companies must comply with a set of standards and regulations related to data protection, IT and employee security, and the functioning of their products. Beyond the penalties for non-compliance —which can be significant—a security breach or unaddressed vulnerability can seriously damage an organization's brand image.

Your management has just approved your information system security policy (ISSP). What now? It's time to draw up your IT security plan, which should detail the actions to be implemented to ensure the ISSP is applied. Defining objectives, monitoring current and future actions, measuring results... All this requires flawless project management.
