1/ Centralize for better management
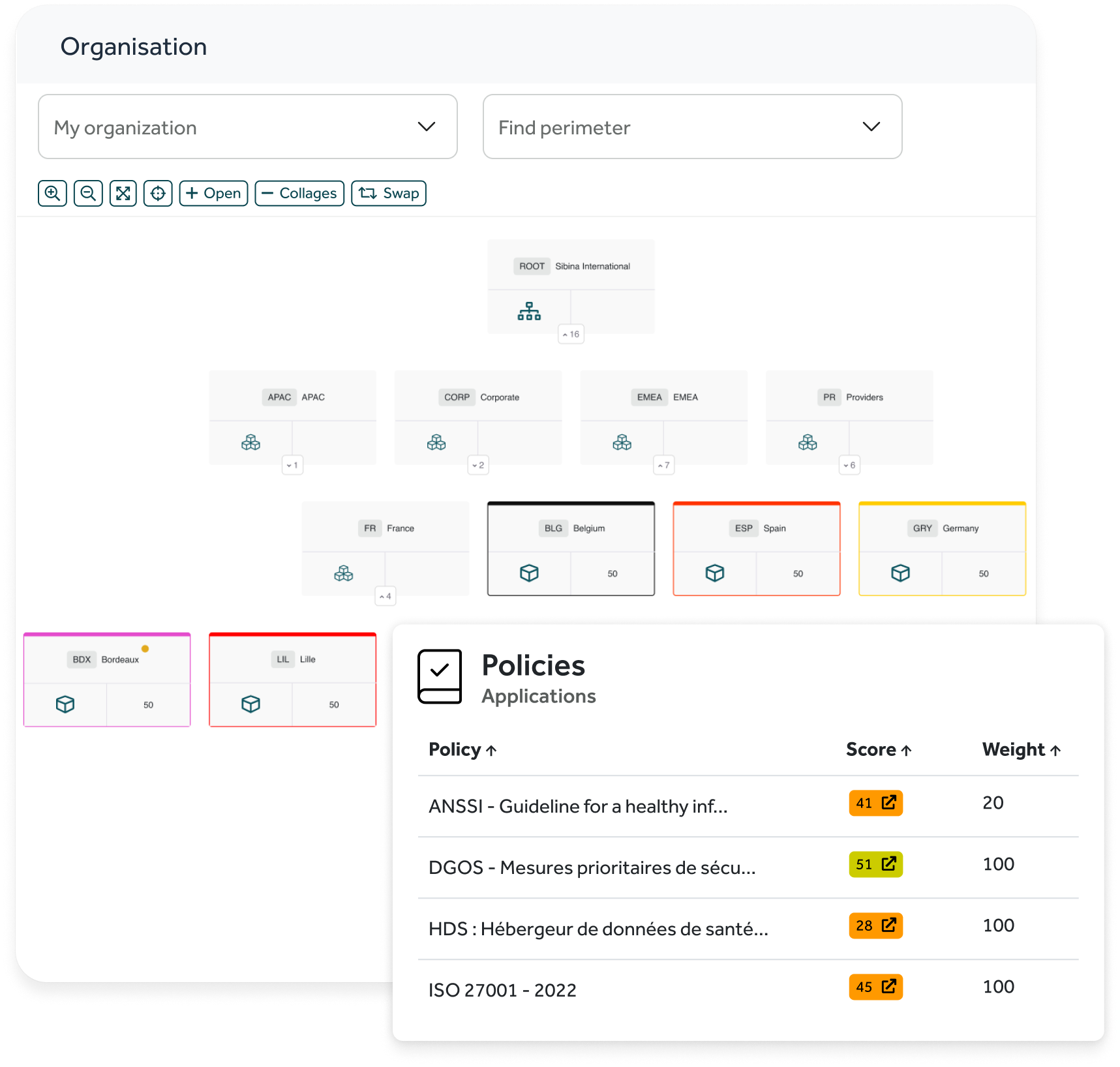
To effectively manage the group's cybersecurity and prioritize its actions, it was essential to have a clear and granular view of Tessi's entire organization:
- Complete mapping of the organization and its 53 areas of operation.
- Consolidated view of security levels at the group, BU, and subsidiary levels.
- Implementation of 22 automated monthly and quarterly indicators, with associated evidence.
Objectives covered:
A clear visualization of internal security and critical applications.
The cyber department now has a consistent view, updated in real time, and each critical application has a dedicated cyber score.
2/ Automate to increase efficiency
Each month, consolidating indicators required a full week of work, just to aggregate the data. Thanks to Tenacy's intelligent modeling and feedback from their connectors, Jérôme Farrouil is able to speed up data processing and make it more reliable.
- Industrialization of level 1 and 2 controls, with integrated workflows.
- Monitoring of more than 500 actions and remediation plans.
- Automation of recurring tasks and automated approvals between local and central teams.
Objectives covered:
Reliable data refreshed in real time.
"Automation means reliability: you know where you stand at all times, without having to chase after Excel files."
Jérôme Farrouil, Group Director of Compliance, Risk, and Cybersecurity at Tessi
3/ Optimize multi-level reporting
The centralization and automation of cyber activities in Tenacy have led to an overall increase in efficiency for operational monitoring and reporting that is always up to date.
- Monitoring changes in indicators over time using historical data
- Dashboards tailored to the needs of the Executive Committee: overall security levels, risk levels
- Operational monitoring and reporting: dashboards dedicated to operational teams to prioritize critical actions
Objectives covered:
Dashboards tailored to each stakeholder and editable in just a few clicks.
"We all speak the same language, from the local CISO to the Executive Committee. It's a real cultural shift."
Jérôme Farrouil, Group Director of Compliance, Risk, and Cybersecurity at Tessi
4/ Facilitate collaboration between teams
With the multitude of tools used by cyber teams and the geographical distance from local CISOs, ensuring smooth communication between teams was a real challenge:
- Centralization of all cyber projects in a single collaborative tool.
- Instant reporting by BU: subsidiary or group, available "live" for audits and clients.
- Cyber committees without PowerPoint: Tenacy dashboards are used directly for dialogue with management.
"If I had to do the same thing with people and Excel files, I would easily need four more people. And above all, I would have a much higher turnover because that would be all the teams would be doing."
Jérôme Farrouil, Group Director of Compliance, Risk, and Cybersecurity at Tessi
5/ Finally, controlled multi-compliance management
{{3-cards}}
45+ built-in frameworks
ISO 27001, PCI DSS, SOC 2, DORA, NIS2, GDPR, cross-referenced with Tessi's internal standards.
Gap analysis
between two frameworks obtained in five minutes: already 82% compliance between PSSI and SOC 2.
Consolidated reporting
and directly exportable for external audits or client committees.
Once data was centralized, processes automated, and exchanges aligned, compliance became an operational and strategic asset rather than a constraint.
Thanks to this consistent architecture, Tessi can now manage all of its repositories from a single, unified environment.

.png)
.jpg)
