" Risk-based approach " and " compliance-based approach ": you've probably heard these terms before. These two English terms can be translated into French as " approche par les risques " and " approche par la conformité " – and they are sure to divide the cyber world.
To put it simply, they refer to the mindset with which the CISO builds their cyber strategy. But how do you choose your camp? And above all, do you really have to choose one?
Risk vs. compliance: a battle at the top?
We could simplify these terms by saying that the first comes from the " fear of getting hurt " (of suffering a cyberattack), while the second comes from the " fear of the police " (of being caught for non-compliance).
Compliance approach: what are we talking about?
Compliance can fall into three distinct areas:
- compliance with best practices (NIST, ANSSI hygiene guide, etc.);
- compliance with applicable regulations;
- compliance with certification requirements.
When you consider that 72% of organizations are affected by at least one regulation (CESIN Barometer) and that certifications are an undeniable business asset, it is clear that compliance is essential.
What does it involve? It can be summarized in four steps:
- identify the regulations or standards to be followed;
- assess the gap between these and the current situation;
- take the necessary steps to close this gap;
- maintain compliance (and correct if necessary).
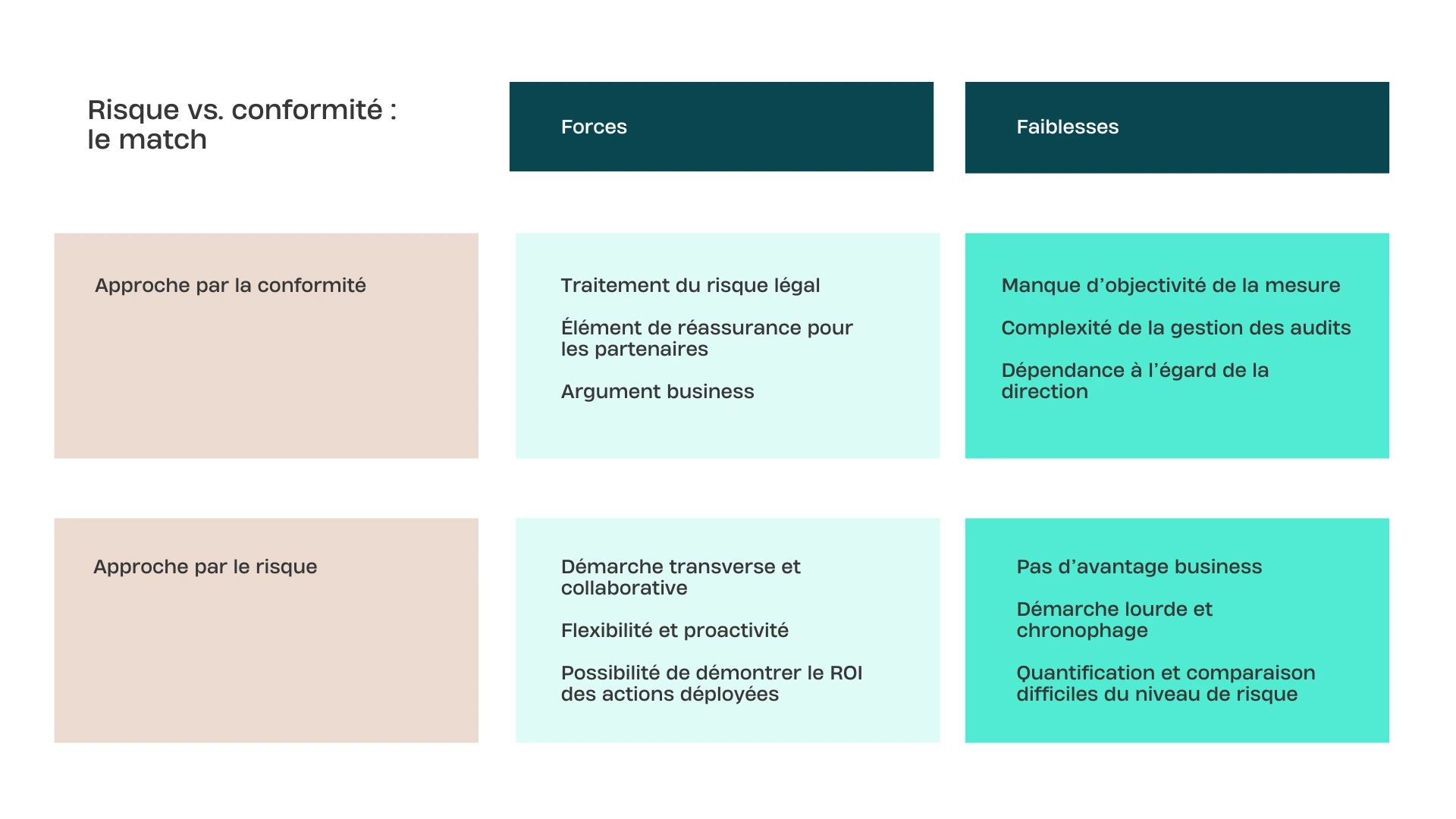
Compliance approach: pros and cons
The main advantage of the compliance approach is twofold: it addresses legal risk while responding to the organization's business challenges.
But it also has its flaws (after all, who doesn't?). Among them is a lack of objectivity in measuring compliance: for the same situation, the compliance rate can vary between 80% and 100%, depending on the person responsible for assessing it...
There is also the complexity of audit management, and above all the heavy reliance on senior management: without the support and legitimization of C-level executives, the CISO may struggle to impose compliance measures that teams do not always see the value of.
Risk-based approach: what are we talking about?
Adopting a risk-based approach involves (again) four steps:
- identify a possible incident scenario;
- analyze the impact that such an incident would have on the various stakeholders within the organization;
- assess the likelihood of this scenario (motives and means of the threat agent, current security level, etc.);
- Implement corrective actions to mitigate this risk (and measure their performance).
Risk-based approach: pros and cons
Unlike the compliance-based approach, the risk-based approach has the advantage of being cross-functional and collaborative. By talking to different departments about THEIR risks, what could happen to them, and how it would impact them, we generally get their attention much more effectively.
The risk-based approach increases flexibility and proactivity, allowingspecific potential threats to be anticipated before they materialize.
The icing on the cake: it is easier to justify cyber investments by demonstrating the ROI of the actions taken, in particular by quantifying the impact that an attack could have had on the organization.
However, this approach has its Achilles' heel—or rather, heels:
- The risk-based approach does not really reassure customers and other external stakeholders (unlike certification).
- the analysis process can be cumbersome and time-consuming, ultimately leaving little time for dealing with the risk itself;
- It is difficult to accurately quantify a company's level of risk, and even more difficult to compare these levels between several entities within an organization.
The hybrid approach: the sweet spot for cyber management?
What if the " compliance approach " and the " risk approach " were ultimately just two steps in a single management strategy? What if they were cumulative rather than exclusive?
That is what the EBIOS RM pyramid seems to be telling us (if pyramids could talk).
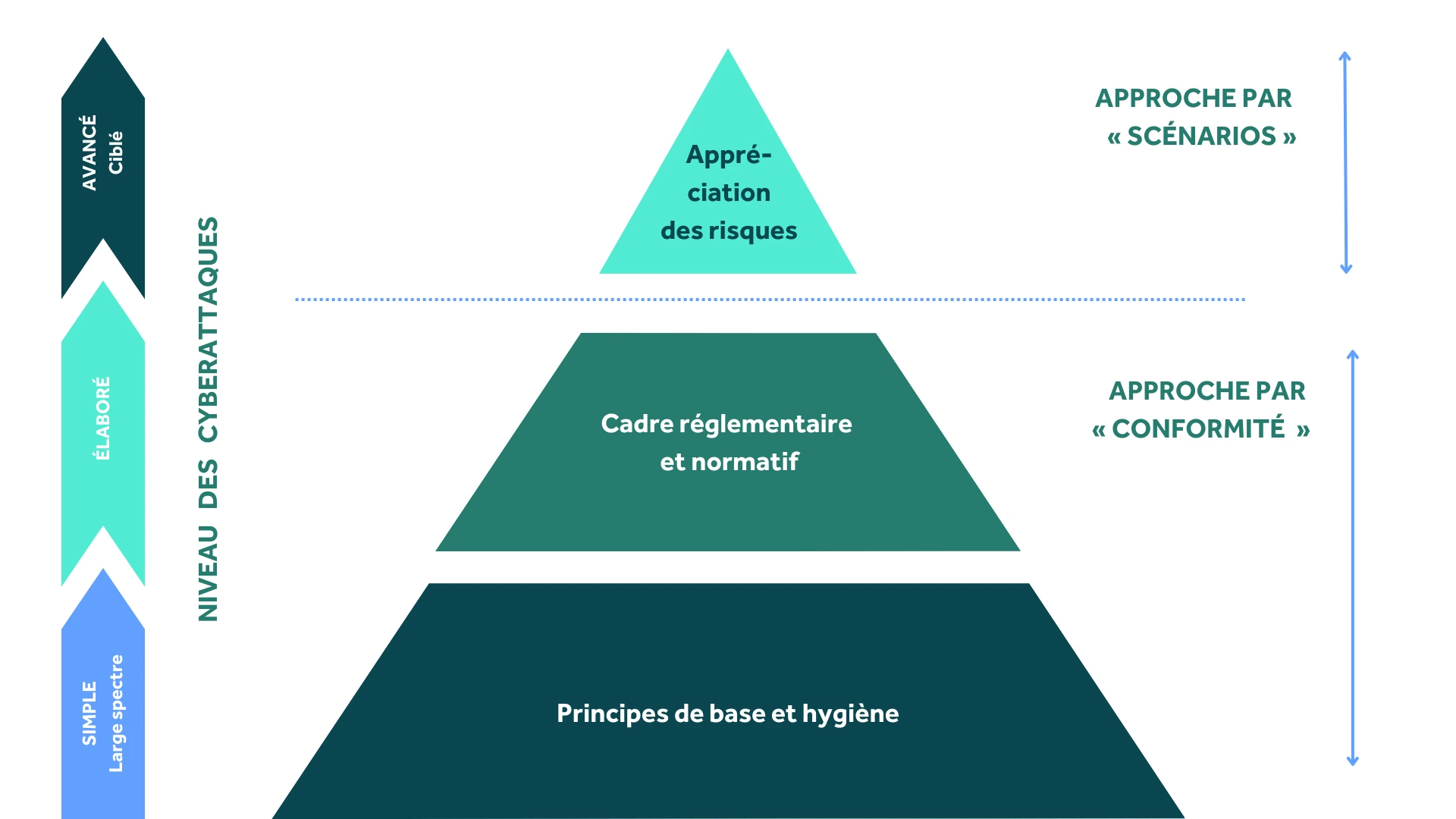
Ultimately, it's all a question of timing and the maturity ofthe organization.
- Initially,the compliance approach allows basic hygiene principles to be established, followed by the integration of the applicable regulatory and normative framework.
- It is in a second phase (or in organizations that already have a high level of cyber maturity) thatthe risk-based approach can be implemented—without, however, putting an end to the compliance process.
The ultimate goal: a hybrid approach that incorporates the compliance foundation while being risk-oriented.
The numbers corner
During our webinar on risk vs. compliance, we asked participants about their preferred approach in their daily work. We found that the hybrid approach was (by far) the winner, adopted by 58% of respondents.
The others shared the rest of the cake with:
- 25% for the compliance approach;
- 8% for the risk-based approach;
- 8% for a so-called "instinctive" approach.
Good news: Tenacy was designed (among other things) to help you balance risk and compliance! Traceability, consistency, reporting, collaboration, knowledge base... the tool includes all the features you need for effective hybrid management.

![[White paper] 5 keys to managing your cybersecurity](https://cdn.prod.website-files.com/68eccb60f9cf9c228c061b75/695f73ba996b3472b4fa4e34_visuel-tenacy%20(2).jpg)

